Showing posts with label removal. Show all posts
Showing posts with label removal. Show all posts
Tuesday, March 28, 2017
Win32 Bundpil Virus Removal Instruction
Win32 Bundpil Virus Removal Instruction
The worm Win32/Bundpil.s, Win32/Bundpil.a or win32/ bundpil.xx or win32.agent bundpil was added by eset on January 10, 2013. The indications that you are infected with this malicious worm is; when opening the flash drive, usb drive, external hard drive or any external storage device, you haven’t seen anything except th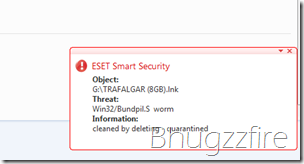 e shortcut link file of the name of your external storage device.Example, if you have a 4 Gb removable drive and you try open it, the drive letter of that certain drive would only show a shortcut link such as xxxx(4gb).lnk (where xxxx is the name of the removable device) and (4gb is the size of the flash drive) and all of your files suddenly disappear. Sometimes you see nothing even the shortcut link icon because it is deleted with your anti virus software.Actually the files in the flash disk wasnt really disappear or deleted. It’s just move to another folder, just click the shortcut link of the drive and you will be redirected to your files. But be aware clicking the shortcut is equivalent of clicking a virus.To fix the problem, update the anti-virus into it’s latest signature. Then run a quick scan to your computer including the infected external storage device . After the worm Win32/Bundpil.s win32/bundpil.xx has been remove, follow the steps below to completely fix and restore your external drive way back before the problem occurs.
e shortcut link file of the name of your external storage device.Example, if you have a 4 Gb removable drive and you try open it, the drive letter of that certain drive would only show a shortcut link such as xxxx(4gb).lnk (where xxxx is the name of the removable device) and (4gb is the size of the flash drive) and all of your files suddenly disappear. Sometimes you see nothing even the shortcut link icon because it is deleted with your anti virus software.Actually the files in the flash disk wasnt really disappear or deleted. It’s just move to another folder, just click the shortcut link of the drive and you will be redirected to your files. But be aware clicking the shortcut is equivalent of clicking a virus.To fix the problem, update the anti-virus into it’s latest signature. Then run a quick scan to your computer including the infected external storage device . After the worm Win32/Bundpil.s win32/bundpil.xx has been remove, follow the steps below to completely fix and restore your external drive way back before the problem occurs.
 e shortcut link file of the name of your external storage device.Example, if you have a 4 Gb removable drive and you try open it, the drive letter of that certain drive would only show a shortcut link such as xxxx(4gb).lnk (where xxxx is the name of the removable device) and (4gb is the size of the flash drive) and all of your files suddenly disappear. Sometimes you see nothing even the shortcut link icon because it is deleted with your anti virus software.Actually the files in the flash disk wasnt really disappear or deleted. It’s just move to another folder, just click the shortcut link of the drive and you will be redirected to your files. But be aware clicking the shortcut is equivalent of clicking a virus.To fix the problem, update the anti-virus into it’s latest signature. Then run a quick scan to your computer including the infected external storage device . After the worm Win32/Bundpil.s win32/bundpil.xx has been remove, follow the steps below to completely fix and restore your external drive way back before the problem occurs.
e shortcut link file of the name of your external storage device.Example, if you have a 4 Gb removable drive and you try open it, the drive letter of that certain drive would only show a shortcut link such as xxxx(4gb).lnk (where xxxx is the name of the removable device) and (4gb is the size of the flash drive) and all of your files suddenly disappear. Sometimes you see nothing even the shortcut link icon because it is deleted with your anti virus software.Actually the files in the flash disk wasnt really disappear or deleted. It’s just move to another folder, just click the shortcut link of the drive and you will be redirected to your files. But be aware clicking the shortcut is equivalent of clicking a virus.To fix the problem, update the anti-virus into it’s latest signature. Then run a quick scan to your computer including the infected external storage device . After the worm Win32/Bundpil.s win32/bundpil.xx has been remove, follow the steps below to completely fix and restore your external drive way back before the problem occurs.But Before you proceed make sure you have select and unhide the following:
- Select Show hidden files, folders, or drives
- Uncheck Hide extensions for known file types
- Unchecked Hide protected operating files (recommended)
All the selection is located in My Computer, Tools, Folder Options Menu.
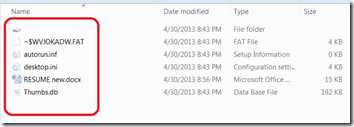
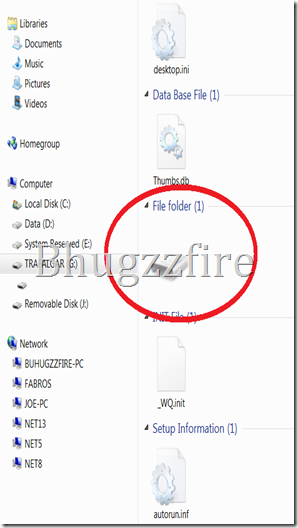 | Open the removable drive and delete the all files except the encircled one. |
Then open the disk like icon, that is the place where all your file move by Win 32 Bundpil.S Worm.
After opening it, select all the files inside, and cut and paste it outside that encircled disk icon.
Delete the disk icon to complete the recovery. Now remove your external drive and put it back again and check if the same problem occurs. If you see your files again, you did it right. You have successfully completed the instruction.
Note: the above procedure such as the disk like icon with no drive letter and the file autorun.inf and _Wq.init are hidden by default. Be sure to follow the above instructions.
Related Articles:
- Watch instruction of fixing infected usb drive video
- Fix external storage device using the Virus Removal tools
- Detailed information of flash drive worm infector
Available link for download
Labels:
bundpil,
instruction,
removal,
virus,
win32
Monday, December 12, 2016
Virus Trojan and Worm Removal as of 2014
Virus Trojan and Worm Removal as of 2014
This is a list of Virus Removal Tool as of January 2014. Just select what type of removal you want. Depending the problem of virus infection you have to select the best antivirus brand of your Windows XP, Windows 7, Windows 8 or Windows Vista Computer system.
The removal procedure of infected system are different since these are different antivirus maker company. Be sure to follow the guide located in their respected websitesClick the link associated with the antivirus software currently installed on your system and follow the prompts or instructions on the website.
AVG
http://www.avg.com/us-en/utilities
Avira
http://www.avira.com/en/support-for-free-knowledgebase-detail/kbid/88
BitDefender
http://kb.bitdefender.com/site/article/333/
CA Antivirus
http://homeofficekb.ca.com/CIDocument.asp?KDId=3125&Preview=0&Return=0&GUID=DF325E0AA0AB4264AF47E4BEA49F571B
Comodo Internet Security
https://support.comodo.com/index.phpm=knowledgebase&_a=viewarticle&kbarticeid=298
Cyber Defender Early Detection Center
http://cyberdefender.custhelp.com/app/answers/detail/a_id/207
eScan
http://www.microworldsystems.com/download/tools/esremove.exe
ESET
http://kb.eset.com/esetkb/index?page=content&id=SOLN2788
FRISK F-PROT Antivirus for Windows
http://www.f-prot.com/support/windows/fpwin_faq/25.html
F-Secure
http://www.f-secure.com/en/web/home_global/support/article/kba/2109/k/uninstall+f+secure/p/1
Kaspersky
http://support.kaspersky.com/kis2010/service?qid=208279463
LavaSoft
http://www.lavasoftsupport.com/index.php?showtopic=28
McAfee
http://download.mcafee.com/products/licensed/cust_support_patches/MCPR.exe
Norman Virus Control/Norman Security Suite
http://www.norman.com/support/support_issue_archive/67798/en
Norton (Symantec )
ftp://symantec.com/public/english_us_canada/removal_tools/Norton_Removal_Tool.exe
Norton Security Scan
ftp://symantec.com/public/english_us_canada/removal_tools/NSSRT.exe
Panda
http://www.pandasecurity.com/resources/sop/UNINSTALLER_08.exe
Panda Cloud Internet Protection
http://www.pandasecurity.com/resources/sop/Cloud_AV_Uninstaller.exe
Pareto Logic
http://techsupport.paretologic.com/plsupport/consumer/kbdetail.asp?kbid=555
Sophos
http://www.sophos.com/support/knowledgebase/article/11019.html
Trend Micro
http://esupport.trendmicro.com/1/How-do-I-remove-old-or-new-versions-of-Trend-Micro-products-in-my-comp.aspx
Trend Micro Titanium
http://esupport.trendmicro.com/solution/en-us/1056455.aspx
Trend Micro Worry-Free Business Security Agent
http://esupport.trendmicro.com/solution/en-us/1057237.aspx
Windows Live OneCare
http://download.microsoft.com/download/4/c/b/4cb845e7-1076-437b-852a-7842a8ab13c8/OneCareCleanUp.exe
Windows Security Essentials
http://support.microsoft.com/kb/2435760
Zone Alarm
http://download.zonealarm.com/bin/free/support/download/clean.exe
Some antivirus removal requires you to reboot your Windows XP or Windows 7 system and start to safe mode. Also prepare for at least 512 Mb external storage device because some removal tools requires you to copy the program into your usb disk and run it as USB Bootable device.
The removal procedure of infected system are different since these are different antivirus maker company. Be sure to follow the guide located in their respected websitesClick the link associated with the antivirus software currently installed on your system and follow the prompts or instructions on the website.
List Of Antivirus Program and Their Removal Tools
Avast
http://files.avast.com/files/eng/aswclear.exe
http://files.avast.com/files/eng/aswclear.exe
AVG
http://www.avg.com/us-en/utilities
Avira
http://www.avira.com/en/support-for-free-knowledgebase-detail/kbid/88
BitDefender
http://kb.bitdefender.com/site/article/333/
CA Antivirus
http://homeofficekb.ca.com/CIDocument.asp?KDId=3125&Preview=0&Return=0&GUID=DF325E0AA0AB4264AF47E4BEA49F571B
Comodo Internet Security
https://support.comodo.com/index.phpm=knowledgebase&_a=viewarticle&kbarticeid=298
Cyber Defender Early Detection Center
http://cyberdefender.custhelp.com/app/answers/detail/a_id/207
eScan
http://www.microworldsystems.com/download/tools/esremove.exe
ESET
http://kb.eset.com/esetkb/index?page=content&id=SOLN2788
FRISK F-PROT Antivirus for Windows
http://www.f-prot.com/support/windows/fpwin_faq/25.html
F-Secure
http://www.f-secure.com/en/web/home_global/support/article/kba/2109/k/uninstall+f+secure/p/1
Kaspersky
http://support.kaspersky.com/kis2010/service?qid=208279463
LavaSoft
http://www.lavasoftsupport.com/index.php?showtopic=28
McAfee
http://download.mcafee.com/products/licensed/cust_support_patches/MCPR.exe
Norman Virus Control/Norman Security Suite
http://www.norman.com/support/support_issue_archive/67798/en
Norton (Symantec )
ftp://symantec.com/public/english_us_canada/removal_tools/Norton_Removal_Tool.exe
Norton Security Scan
ftp://symantec.com/public/english_us_canada/removal_tools/NSSRT.exe
Panda
http://www.pandasecurity.com/resources/sop/UNINSTALLER_08.exe
Panda Cloud Internet Protection
http://www.pandasecurity.com/resources/sop/Cloud_AV_Uninstaller.exe
Pareto Logic
http://techsupport.paretologic.com/plsupport/consumer/kbdetail.asp?kbid=555
Sophos
http://www.sophos.com/support/knowledgebase/article/11019.html
Trend Micro
http://esupport.trendmicro.com/1/How-do-I-remove-old-or-new-versions-of-Trend-Micro-products-in-my-comp.aspx
Trend Micro Titanium
http://esupport.trendmicro.com/solution/en-us/1056455.aspx
Trend Micro Worry-Free Business Security Agent
http://esupport.trendmicro.com/solution/en-us/1057237.aspx
Windows Live OneCare
http://download.microsoft.com/download/4/c/b/4cb845e7-1076-437b-852a-7842a8ab13c8/OneCareCleanUp.exe
Windows Security Essentials
http://support.microsoft.com/kb/2435760
Zone Alarm
http://download.zonealarm.com/bin/free/support/download/clean.exe
Some antivirus removal requires you to reboot your Windows XP or Windows 7 system and start to safe mode. Also prepare for at least 512 Mb external storage device because some removal tools requires you to copy the program into your usb disk and run it as USB Bootable device.
Available link for download
Wednesday, December 7, 2016
The Win32 Flashbot and Win32 Malagent Virus Removal
The Win32 Flashbot and Win32 Malagent Virus Removal
The Win32/Flashbot.A Worm, Trojan Win32/Malagent (Microsoft), Variant.Strictor.2025 (Bitdefender) is a kind of worm that spreads via removable media such as flash drive, external drive, memory card, etc.
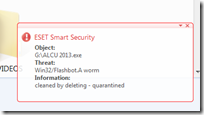 The worm searches for files and folders in the root folders of removable drives. It copies itself into the root folders of removable drives using the same filename of the existing files and folder. The extension of the file or folder will become ".exe" and the original content were hidden. When the infected file is executed, the original file is also run.Before you proceed make sure you have select and unhide the following
The worm searches for files and folders in the root folders of removable drives. It copies itself into the root folders of removable drives using the same filename of the existing files and folder. The extension of the file or folder will become ".exe" and the original content were hidden. When the infected file is executed, the original file is also run.Before you proceed make sure you have select and unhide the following
All the selection is located in My Computer, Tools, Folder Options Menu.
To fix the problem:
To unhide the folder
 The worm searches for files and folders in the root folders of removable drives. It copies itself into the root folders of removable drives using the same filename of the existing files and folder. The extension of the file or folder will become ".exe" and the original content were hidden. When the infected file is executed, the original file is also run.Before you proceed make sure you have select and unhide the following
The worm searches for files and folders in the root folders of removable drives. It copies itself into the root folders of removable drives using the same filename of the existing files and folder. The extension of the file or folder will become ".exe" and the original content were hidden. When the infected file is executed, the original file is also run.Before you proceed make sure you have select and unhide the following- Select Show hidden files, folders, or drives
- Uncheck Hide extensions for known file types
- Unchecked Hide protected operating files (recommended)
All the selection is located in My Computer, Tools, Folder Options Menu.
To fix the problem:
- Update the anti-virus into it’s latest virus signature
- Run a quick scan in your computer
- Run infected external storage; the “.exe” will automatically deleted
- Unhide file and folder in removable drive
To unhide the folder
- Right click the hidden file or folder
- Click Properties
- Uncheck or deselect “Hidden" and “Read-only”
The Removable Drive infected with Win32 Flashbot Worm
Available link for download
Wednesday, November 30, 2016
The Win32 Ramnit Virus Detection and Removal
The Win32 Ramnit Virus Detection and Removal
Win32/Ramnit is a file infector detected in July 2010. It is also a virus in the same family as Virut, Sality and virtob. It attacks Windows XP, Windows Vista, Windows 7 executable files, it infects those with the extensions .exe, .dll and .html and it can also be distributed via external removable drives such as fllash disk, etc
.
When executed, the virus copies itself in some of the the following locations
The following Registry entries are set:
The virus creates and runs a new thread with its own program code within the following processes:
The host file is modified in a way that causes the virus to be executed prior to running the original code. The size of the inserted code is 53 KB .
The Windows Shell allows local users or remote attackers to execute arbitrary code via a crafted *.lnk, *.pif shortcut file when its icon is displayed.
No further user interaction is required to execute arbitrary code.
The virus acquires data and commands from a remote computer or the Internet.
The virus contains a list of addresses.
It can execute the following operations:
The virus may create the following files:
The virus connects to the following addresses:
The virus may create and run a new thread with its own program code within any running process.
After the Win32 Ramnit worm virus removed. Follow the steps below to completely restore your external drive way back before the problem occured.
.

Other Virus Aliases
W32/Infector.Gen2 (Avira)- Win32/Ramnit.A (CA) Win32/Ramnit.AY (ESET),Win32/Ramnit.F (Eset),Win32.Rmnet (Dr.Web), W32.Infector (Ikarus), W32/Ramnit.a (McAfee), W32/Patched-I (Sophos), PE_RAMNIT.A (Trend Micro),Type_Win32 (Kaspersky), Win32/Zbot.A (AVG)
Virus execution
- %programfiles%MicrosoftWaterMark.exe
- %commonprogramfiles%MicrosoftWaterMark.exe
- %appdata%MicrosoftWaterMark.exe
- %system%MicrosoftWaterMark.exe
- %windir%MicrosoftWaterMark.exe
- %temp%MicrosoftWaterMark.exe
- %homedrive%%homepath%MicrosoftWaterMark.exe
The following Registry entries are set:
- [HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionWinlogon]
- "Userinit" = "%originalvalue%, %malwarefolder%MicrosoftWaterMark.exe"
This causes the virus to be executed on every system start.
The virus creates and runs a new thread with its own program code within the following processes:
- Svchost.exe
- Executable file infection
- The virus searches local drives for files with the following file extensions:
- .exe
- .dll
- RMNetwork
- Files are infected by adding a new section that contains the virus .
The host file is modified in a way that causes the virus to be executed prior to running the original code. The size of the inserted code is 53 KB .
Virus File infection
- The virus searches local drives for files with the following file extensions:
- .htm
- .html
The Windows Shell allows local users or remote attackers to execute arbitrary code via a crafted *.lnk, *.pif shortcut file when its icon is displayed.
No further user interaction is required to execute arbitrary code.
The virus creates the following files:

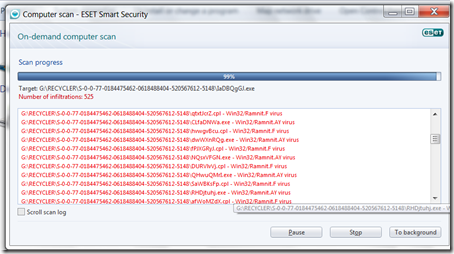
- %removabledrive%RECYCLERS-7-1-36-6133081425-6700277004-675130086-4217%variable1%.exe
- %removabledrive%RECYCLERS-7-1-36-6133081425-6700277004-675130086-4217%variable2%.cpl
- %removabledrive%autorun.inf
- %removabledrive%Copy of Shortcut to (1).lnk
- %removabledrive%Copy of Shortcut to (2).lnk
- %removabledrive%Copy of Shortcut to (3).lnk
- %removabledrive%Copy of Shortcut to (4).lnk
The virus acquires data and commands from a remote computer or the Internet.
The virus contains a list of addresses.
It can execute the following operations:
- capture screenshots
- send gathered information
- download files from a remote computer and/or the Internet
- run executable files
- shut down/restart the computer
The virus may create the following files:
- %system%dmlconf.dat
The virus connects to the following addresses:
- google.com
- bing.com
- yahoo.com
The virus may create and run a new thread with its own program code within any running process.
The Virus Removal
To fix the issue:- update the anti-virus into it’s latest signature
- Then run a quick scan in your computer
- Run infected external storage
After the Win32 Ramnit worm virus removed. Follow the steps below to completely restore your external drive way back before the problem occured.
- Open the external drive
- Delete all files except the drive icon that have no drive letter
- Open the drive icon with no drive letter
- Select all your files and cut or copy
- Then go back to my computer
- Open external storage device (that is, flash drive, usb drive, external hard disk or whatever it is)
- Paste your file
- Then, delete the “the drive icon that have no drive letter”
Before you proceed make sure the following Folder Options Menu are selected:
- Select Show hidden files, folders, or drives
- Uncheck Hide extensions for known file types
- Unchecked Hide protected operating files (recommended)
Available link for download
Wednesday, November 9, 2016
Win32 Sality Worm Virus Complete Removal Instruction
Win32 Sality Worm Virus Complete Removal Instruction
When the Worm Win32 Sality strike into my computer, it causes me headache. All uncompressed executable file I have save to my computer were all infected and cant used anymore. But the real problem wasnt stop there, all the computer connected in the network were also infected.
At that time of infection, there are limited updates and removal tool available in the web and most of the tools were only good for prevention (not those computer already infected).The thing I did at that time was isolate the infected computer in the network ad backup all important files (win32 sality was not include at backup). Then I Format and reprogram the computer; install and update antivirus definitions.
This solution comes into my mind because its the fastest way to remove the win32 sality worm rather than removing entries in Windows Registry.
So what is Win32 Sality?
A Win32 Sality worn is a family of polymorphic file infectors that target Windows executable files with 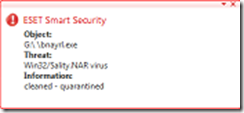 extensions .SCR or .EXE. They may execute a damaging payload that deletes files with for executable files and will attach its code previously processed. It will also infects computer connected to the network rapidly. It also infect the system such as telnet.exe, write.exe, regedt32.exe, cmd.exe, notepad.exe files and run in memory processes making it complicated to remove.
extensions .SCR or .EXE. They may execute a damaging payload that deletes files with for executable files and will attach its code previously processed. It will also infects computer connected to the network rapidly. It also infect the system such as telnet.exe, write.exe, regedt32.exe, cmd.exe, notepad.exe files and run in memory processes making it complicated to remove.
 extensions .SCR or .EXE. They may execute a damaging payload that deletes files with for executable files and will attach its code previously processed. It will also infects computer connected to the network rapidly. It also infect the system such as telnet.exe, write.exe, regedt32.exe, cmd.exe, notepad.exe files and run in memory processes making it complicated to remove.
extensions .SCR or .EXE. They may execute a damaging payload that deletes files with for executable files and will attach its code previously processed. It will also infects computer connected to the network rapidly. It also infect the system such as telnet.exe, write.exe, regedt32.exe, cmd.exe, notepad.exe files and run in memory processes making it complicated to remove.Causes
- Installed via links in undesirable e-mail attachments
- Infected Removable device inserted into good computer
- Network computer is infected
The Symptoms
- Blue screen when trying to enter in Safe Mode
- When opening executable files infected NSIS error appear
- Removable disk drives contains Autorun.inf which have random strings and shell commands lines pointing to a file in same folder
- For example the executable files of the installer is 20 Mb, It will be reduce or modified to around 160 Kbytes
Removal Instruction
- Always Update the Virus Definitions
- Run Win32 Sality Removal Tools
Removal instruction (with extra caution)
Registry Editing:- Go to Start Menu
- Click Run (Windows XP) Search (Windows Vista and Windows 7)
- Type Regedit
- Press Enter
- Then locate and delete these registry entries.
Delete the following registry key
- amsint32 located at
HKEY_LOCAL_MACHINESYSTEMControlSet001Services - amsint32 located at
HKEY_LOCAL_MACHINESYSTEMControlSet002Services - amsint32 located at
HKEY_LOCAL_MACHINESYSTEMControlSet003Services - Qurdk located at
HKEY_CURRENT_USERSoftware
Note: Before removing the registry entries, you must have first update your antivirus or run a complete scan using the removal tools
Clik here to download removal tools
Available link for download
Subscribe to:
Posts (Atom)
